Traditional banking security models built on passwords, devices, and static biometrics are no longer sufficient against AI-enabled fraud and social engineering. This blog explains why identity-based controls are failing, how behavioral biometrics enables continuous intent verification, and how financial institutions can reduce fraud losses and false positives by shifting to behavior-driven security.
The traditional banking security model—predicated on validating static credentials and devices—is functionally obsolete in the face of industrialized cybercrime and generative AI. Financial institutions must pivot from point-in-time identity checks to continuous intent verification. Behavioral biometrics offers the only viable path to securing the digital journey by analyzing how a user interacts, not just what they know, reducing fraud losses while dramatically lowering false positive rates.
In this blog, we outline the structural weaknesses in legacy fraud controls, explain how behavioral biometrics shifts security from static identity checks to continuous intent verification, and provide a practical roadmap for financial institutions to adopt this model.
Why Traditional Banking Fraud Controls and Static Authentication Are Failing
If you occupy the C-suite of a financial institution today, you are likely managing a costly paradox: investment in identity access management (IAM) and fraud prevention tools has never been higher, yet fraud losses continue to accelerate. Global e-commerce fraud losses alone were projected to exceed USD 6.4 billion in 2024, driven by sophisticated account takeover (ATO) and synthetic identity attacks.
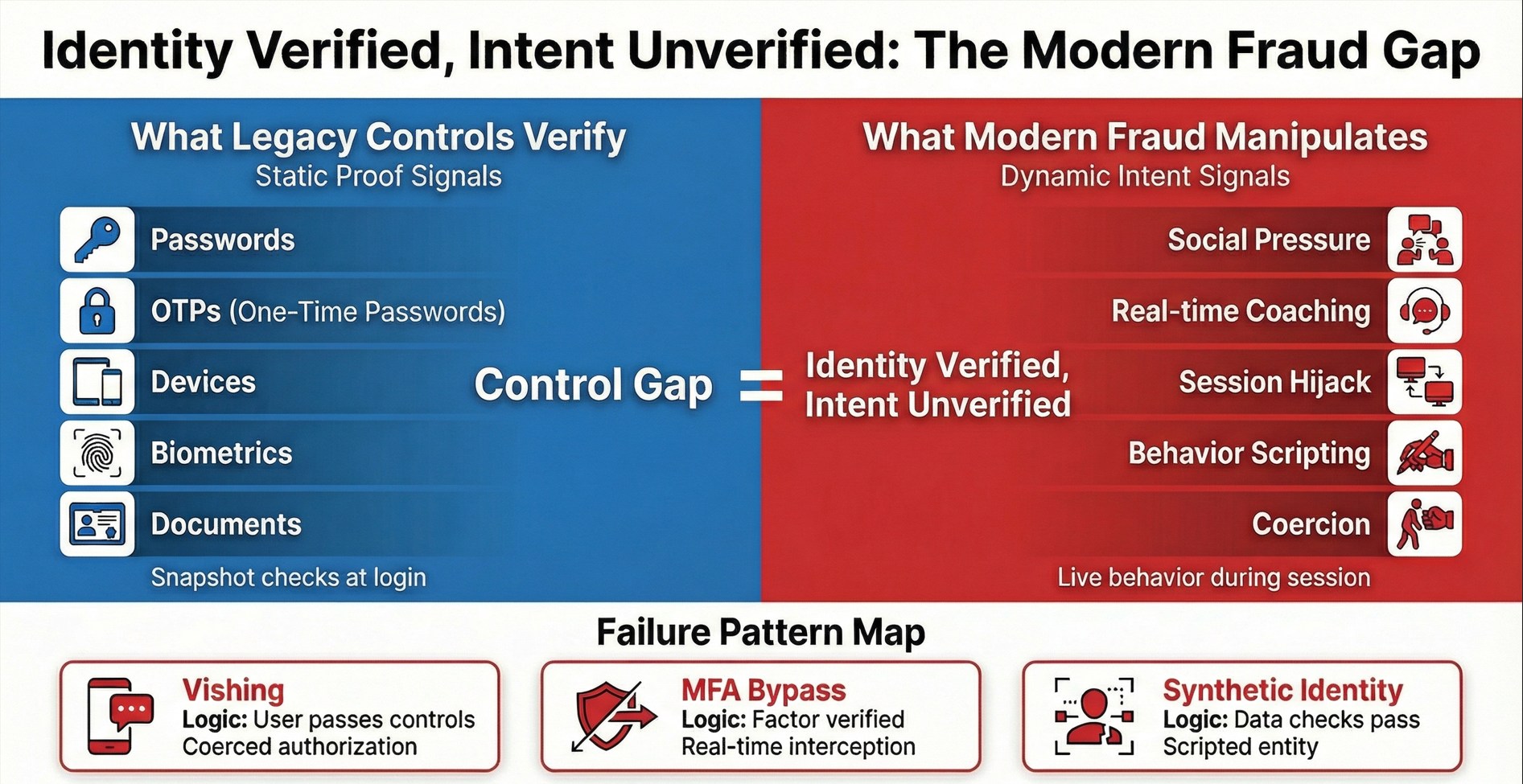
The uncomfortable truth is that your current “fraud detection” stack is failing because it was designed to validate the authenticity of data (passwords, OTPs, device IDs), whereas modern threat actors excel at manipulating the authenticity of intent.
1. Authorized Push Payment (APP) and Social Engineering Fraud Are Bypassing Bank Controls
The most pervasive threats today—Authorized Push Payment (APP) fraud and sophisticated vishing (voice phishing)—bypass traditional firewalls entirely. In these scenarios, the customer is socially engineered into authorizing the transaction themselves. Legacy systems see a valid device, a correct password, and a valid biometric login (like a fingerprint). They approve the transaction because they cannot detect the hesitation, the erratic mouse movements, or the “coercion signals” that indicate a human under duress.
2. Why Multi-Factor Authentication (MFA) Alone No Longer Stops Modern Fraud
MFA was intended to be the silver bullet, but it has become a speed bump. Attackers now use real-time relay attacks and OTP interception bots to bypass these controls. Furthermore, relying heavily on MFA creates significant customer friction. Rules-based systems often treat every user the same, ignoring behavioral context, which results in 98% of Anti-Money Laundering (AML) alerts being false positives—a massive drain on operational resources.
3. The Synthetic Identity Blind Spot
Synthetic identity fraud—where criminals combine real (stolen) SSNs with fabricated names and addresses—is designed to bypass “Know Your Customer” (KYC) checks. These “Frankenstein” identities have no prior bad history and often spend months building legitimate credit scores before a “bust-out” occurs. Static checks welcome them as new growth; they lack the behavioral nuance to see them as bots or scripts.
What Is Behavioral Biometrics in Banking Fraud Detection?
Behavioral biometrics represents a fundamental shift from asking “Who are you?” to asking “Are you acting like yourself—right now?”.
Unlike physiological biometrics (fingerprints, face ID), which are static and can be stolen or spoofed, behavioral biometrics analyze the dynamic, subconscious rhythms of human interaction with a device. These patterns are born from muscle memory and cognitive habits, making them exceptionally difficult for bots or fraudsters to replicate continuously.
How Behavioral Biometrics Detects Fraud Through User Interaction Patterns
- Keystroke Dynamics
It is not about what is being typed, but how. The system measures “flight time” (the milliseconds between key presses) and “dwell time” (how long a key is held down). A fraudster typing a stolen password or using a script will have a mechanical, linear rhythm compared to the fluid, subconscious rhythm of the genuine owner. - Mouse and Cursor Movement
Humans move mice in curved arcs with micro-hesitations (jitter). Bots move in straight lines or with mathematical perfection. Behavioral analytics track velocity, trajectory, and click patterns to instantly distinguish between a human hand and an automated script. - Mobile Interaction (Gyroscopic/Touch)
On smartphones, the technology analyzes the angle at which the phone is held (using the accelerometer and gyroscope), the surface area of the finger tap, and even the user’s gait if they are walking while banking. - Cognitive Patterns
This measures navigation fluency. Does the user hesitate before entering their own home address? Do they navigate directly to a high-value transfer page without checking a balance? These cognitive anomalies are high-fidelity signals of account takeover or synthetic identities.
Behavioral Biometrics vs Rule-Based Fraud Detection Systems
Below is a detailed comparison of how behavioral biometrics handles specific, high-value threat vectors compared to traditional rule-based systems.
| Threat Scenario | Legacy Detection Response | Behavioral Biometrics Response |
|---|---|---|
| Account Takeover (ATO) | FAIL | Attacker enters valid credentials. System sees a correct password and recognized device (via spoofing). Access granted. | DETECT | The system notes the typing rhythm is 40% slower than the user’s baseline and mouse movements are erratic. Action – Step-up auth or block. |
| Social Engineering (Vishing) | FAIL | The victim logs in and enters a valid OTP under duress. The transaction is technically “authorized.” | DETECT | The system detects “coercion signals”—mouse shaking, long pauses before clicking “Submit,” and unusual navigation flow. Action – Delay transaction for review. |
| Synthetic Identity Onboarding | FAIL | Applicant passes credit bureau checks because the synthetic ID has a valid (stolen) SSN and good credit history. | DETECT | The applicant uses “copy-paste” shortcuts for personal data (name/address) or navigates the form with robotic fluency. Action – Flag for manual KYC review. |
| Remote Access Tools (RATs) | FAIL | The device fingerprint matches the customer’s known laptop. | DETECT | The system identifies that mouse and keyboard inputs are injecting directly into the OS, bypassing physical hardware drivers. Action – Terminate session. |
The business impact extends beyond fraud prevention. By using behavioral signals to continuously authenticate users in the background, banks can reduce reliance on intrusive step-up challenges (like OTPs) for low-risk sessions. This “passive” security reduces customer friction and abandonment rates. Furthermore, advanced behavioral models have shown classification accuracy rates as high as 99.24% in separating genuine users from impostors, significantly reducing the operational cost of false positive investigations.
Behavioral Biometrics Implementation Risks
While the technology is transformative, C-suite leaders must navigate significant implementation hurdles regarding privacy, data governance, and algorithmic bias.
1. The Privacy Challenge (GDPR & Compliance)
Behavioral data is highly sensitive. Under the General Data Protection Regulation (GDPR) in the EU and similar laws globally (like Brazil’s LGPD), biometric data used for identification is classified as “special category” data. Processing this data without a lawful basis can lead to massive fines.
Therefore, you must establish a clear lawful basis, often “substantial public interest” (fraud prevention) or explicit consent. Data must be minimized—collecting only what is necessary—and ideally processed using “privacy-preserving” architectures that encrypt behavioral templates so they cannot be reverse-engineered to reveal user identity.
2. The “Cold Start” Problem
Behavioral biometrics rely on a baseline profile. How do you protect a new customer (or a new device) that has no history?
The solution is Hybrid modeling. In the absence of an individual profile, the system compares the user’s behavior against “general population norms” or “cohort models”. For example, no human types at 1,000 characters per minute; flagging this requires no personal history, only a generic understanding of human physiological limits.
3. Algorithmic Bias and Fairness
There is a documented risk that biometric algorithms may perform differently across demographic groups (age, gender, ethnicity), potentially leading to higher false rejection rates for certain customers. To overcome this, ask your vendors for “fairness audits.”
Ensure the underlying machine learning models are trained on diverse datasets. Continuous monitoring of False Rejection Rates (FRR) across different customer segments is essential to ensure equitable access to banking services.
Behavioral Biometrics Adoption Roadmap for Banks
Implementing behavioral biometrics is not just an IT upgrade; it is a strategic move toward a Continuous Trust Architecture. Here is a checklist for the next 6–12 months:
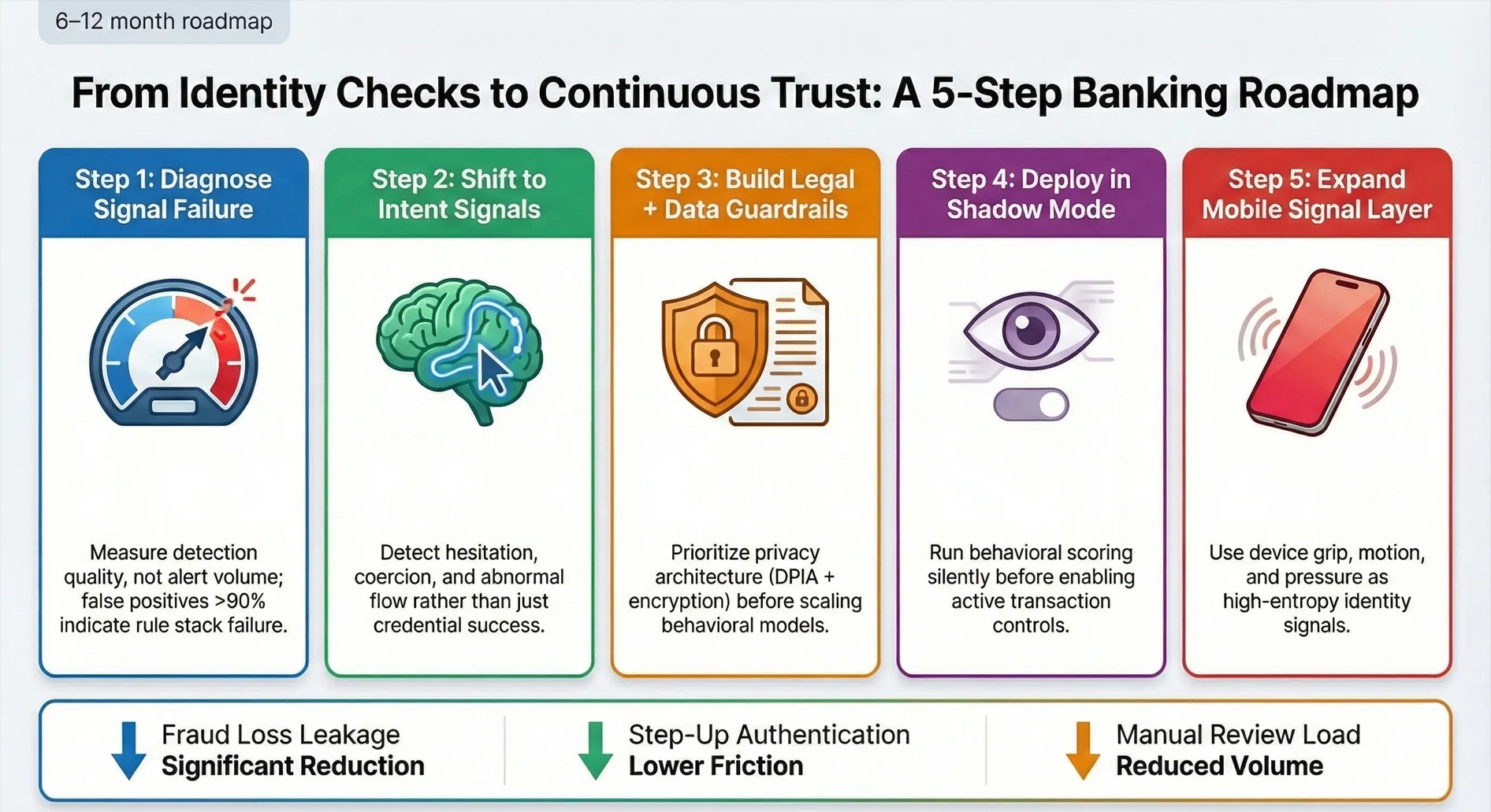
- Audit Your False Positives
If your fraud team is spending more time reviewing legitimate transactions than actual fraud (recall the 98% AML false positive rate), your current rules engine is costing you growth. - Define “Intent” Metrics
Challenge your fraud vendors. Do not just ask if they can detect a bot; ask if they can detect a human under duress. This is the frontier of APP fraud defense. - Review Privacy Governance
Engage legal counsel early. Conduct a Data Protection Impact Assessment (DPIA) to ensure your collection of behavioral data (mouse moves, typing) complies with GDPR Article 9 and local regulations. - Start with Passive Mode
Do not switch to “active blocking” immediately. Deploy the solution in “read-only” mode to build user profiles and establish baseline behavior without disrupting customer experience. - Integrate Mobile Telemetry
Ensure your mobile banking app is capturing gyroscope and accelerometer data. As mobile becomes the primary channel, “how” a customer holds their phone is as important as their password.
Conclusion
We are entering the post-password era. The assumption that a user is safe simply because they logged in successfully is the most dangerous fallacy in modern banking. Fraud has evolved from hacking systems to hacking humans, and from stealing data to mimicking identities.
To protect your institution’s capital and your customers’ trust, security must move from the perimeter to the person. It must become continuous, invisible, and inherently human. Behavioral biometrics offers the only viable path to securing digital sessions in real-time without sacrificing the seamless experience your customers demand.
Anaptyss helps banks implement behavioral-biometrics-driven fraud detection that reduces fraud losses and customer friction — contact us at info@anaptyss.com.



