Transaction laundering allows criminals to process illicit payments through legitimate merchant acquirers, posing significant AML compliance challenges. This blog explains the impact of transaction laundering on financial institutions and outlines strategies to mitigate these risks, ensuring robust financial crime compliance.
Transaction laundering is a process through which unknown entities use and process their payments through facilities provided by a merchant acquirer meant for a known acquirer. Transaction laundering is a criminal activity wherein the perpetrator goes against the merchant’s agreement with the acquirer to hide illegal transactions within seemingly legitimate ones, making it difficult for authorities to trace the illicit funds.
In this blog, we will understand the impact of transaction laundering on the AML compliance efforts of banks and financial institutions and outline the strategies to mitigate transaction laundering for financial crime compliance.
Impact of Transaction Laundering on Financial Services
Transaction laundering can have severe consequences for financial services.
The amount of money laundered globally is equivalent to $800 billion–$2 trillion in current US dollars, estimated to be between 2–5% of the global GDP.
It exposes the merchant services providers (MSPs) to legal and reputational risks and undermines the effectiveness of AML compliance efforts. Transaction laundering creates a situation where MSPs unknowingly become a party to allow illicit funds to flow through their systems undetected and facilitate criminal activities, such as money laundering, financing of terrorism, drug trafficking, etc.
The ultimate damages are borne by the acquiring bank if they fail to comply with anti-money laundering (AML) obligations. These include:
- Chargebacks
- Hefty regulatory penalties
- Damage to reputation
- Loss of customer trust
- Criminal charges and legal actions
Therefore, banks and financial institutions need to understand the intricacies of transaction laundering and implement robust AML compliance measures to protect their institution and ensure a safer financial services environment.
Explore how institutions are enhancing their AML programs with real-time payment fraud detection to stay ahead of evolving laundering tactics.
How Transaction Laundering Works
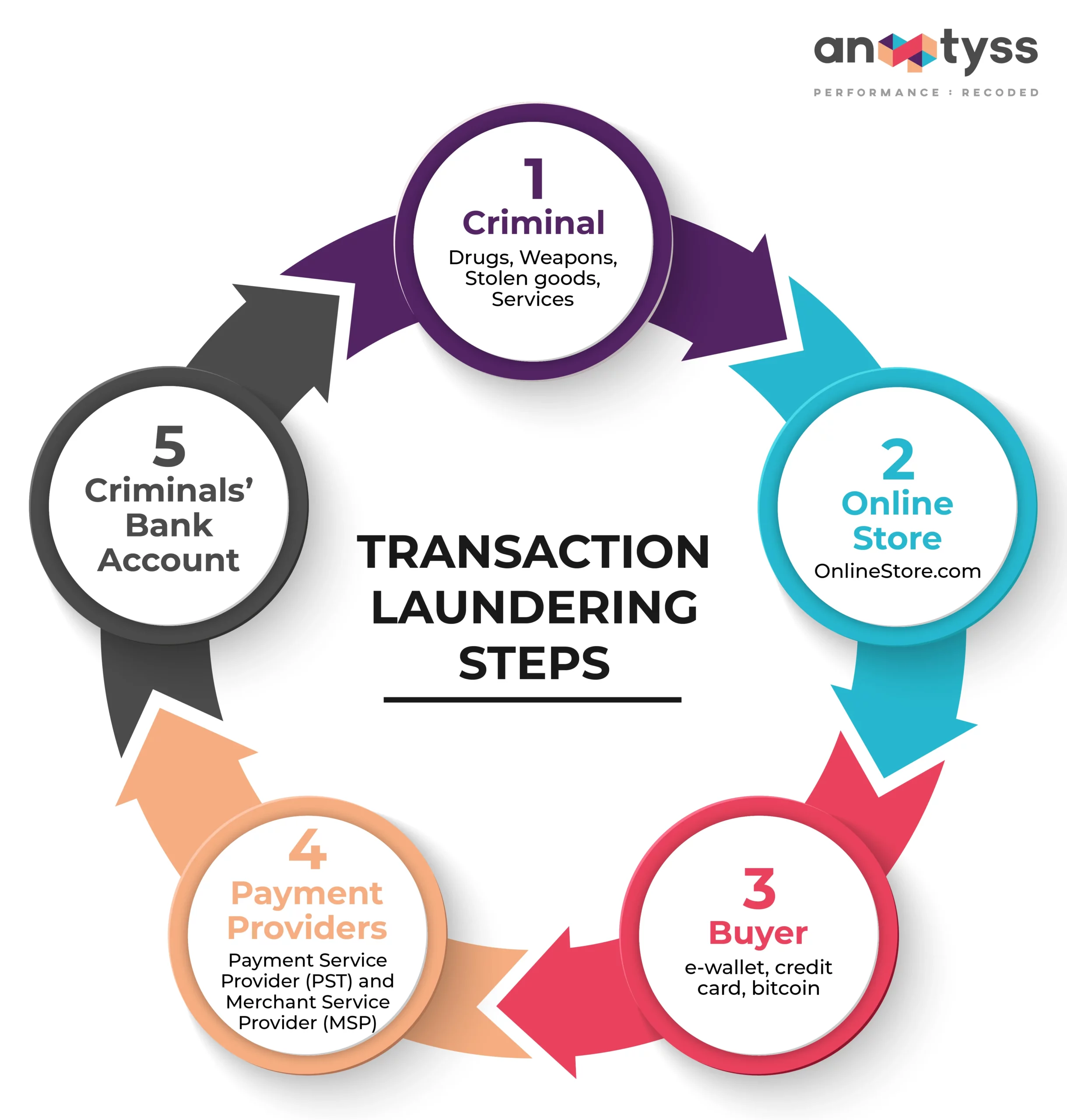
Transaction laundering, also referred to as ‘unauthorized aggregation’ or ‘undisclosed aggregation,’ involves a series of steps to conceal the illicit funds and their origins.
Step 1: Setting Up a Shell Company
Criminals employ various techniques for transaction laundering, such as setting up a shell company and using sophisticated online platforms (legitimate online e-commerce stores or websites).
Step 2: Listing and Selling Illicit Goods
Criminals use the websites to sell illicit goods, such as drugs, services, stolen credit card details, PIIs, and other illegal services.
Step 3: Payment Processing
The buyer is redirected to the online payment portal linked to the e-commerce site. The payments are directed through the legit payment service providers (PSPs) or MSPs which process the payment, transfer it to the receiving bank, and finally, the funds are deposited into the bank account of the criminal entity, making it appear as if the transactions are legitimate.
The business or e-commerce platform is registered with banks or PSPs. Due to ineffective or insufficient controls to detect suspicious activities and patterns, the PSP believes the business to be genuine and allows the transactions.
Further, criminals may also manipulate transaction details to disguise the true nature of the funds. By exploiting vulnerabilities in payment systems, transaction launderers can bypass AML controls and move illegal funds across borders.
Unfortunately, MSPs/PSPs and customers are often unaware of their involvement in this criminal activity.
6 Key Challenges in Identifying Transaction Laundering Activities
Transaction laundering is another way of money laundering that is difficult to detect through traditional internal controls and processes. Below are some prominent challenges that make it tricky to detect and identify transaction laundering activities:
1. Different Risk Profiles
Criminals use new payment methods for transaction laundering, such as cryptocurrencies, e-wallets, and other fintech innovations. These payment methods are constantly emerging and have different risk profiles when compared to traditional payment methods, making it challenging for PSPs and MSPs to effectively monitor and respond to anomalies.
2. Complex Payment Chains and High-Volume Transactions
Transaction laundering involves high transaction volumes, large numbers of small transactions, multiple gateways, and processors. The resultant payment cycle intricacies increase the difficulties of distinguishing between legitimate and illegitimate transactions and identifying suspicious patterns in real-time.
3. Website Security Gaps
Merchants may not be aware or realize that their websites are being used for illegal transactions through affiliate programs or as shadow sites. Limited or insufficient resources for monitoring and investigation may lead to such security gaps and allow criminals to carry out their transactions and money laundering operations.
4. Advanced Techniques to Evade Detection
Money launderers and criminals use sophisticated and advanced techniques, such as anonymization and encryption, to hide illicit transactions and make it difficult for banks to monitor or detect anomalies and suspicious transactions.
5. Unreported Websites
Banks and other financial institutions may not be aware of hidden websites exploited by criminals for transaction laundering. Traditional monitoring methods may fail to identify these unreported platforms.
In addition, creating a professional-looking website has become easier with a Checkout page. Criminals launch their exploits through such bogus websites to build an illegitimate online marketplace and execute money laundering activities digitally. New websites often remain undetected long enough for criminals to conduct their operations.
6. Complexities of Cross-Border Transactions
Cross-border transaction introduces various complexities due to differing regulations, cultural nuances, currencies, and local laws, making it challenging for the PSPs and MSPs to develop a universal detection method or criteria.
Identifying Red Flags for Transaction Laundering
Financial institutions and businesses can look for the following red flags that may indicate potential transaction laundering activities.
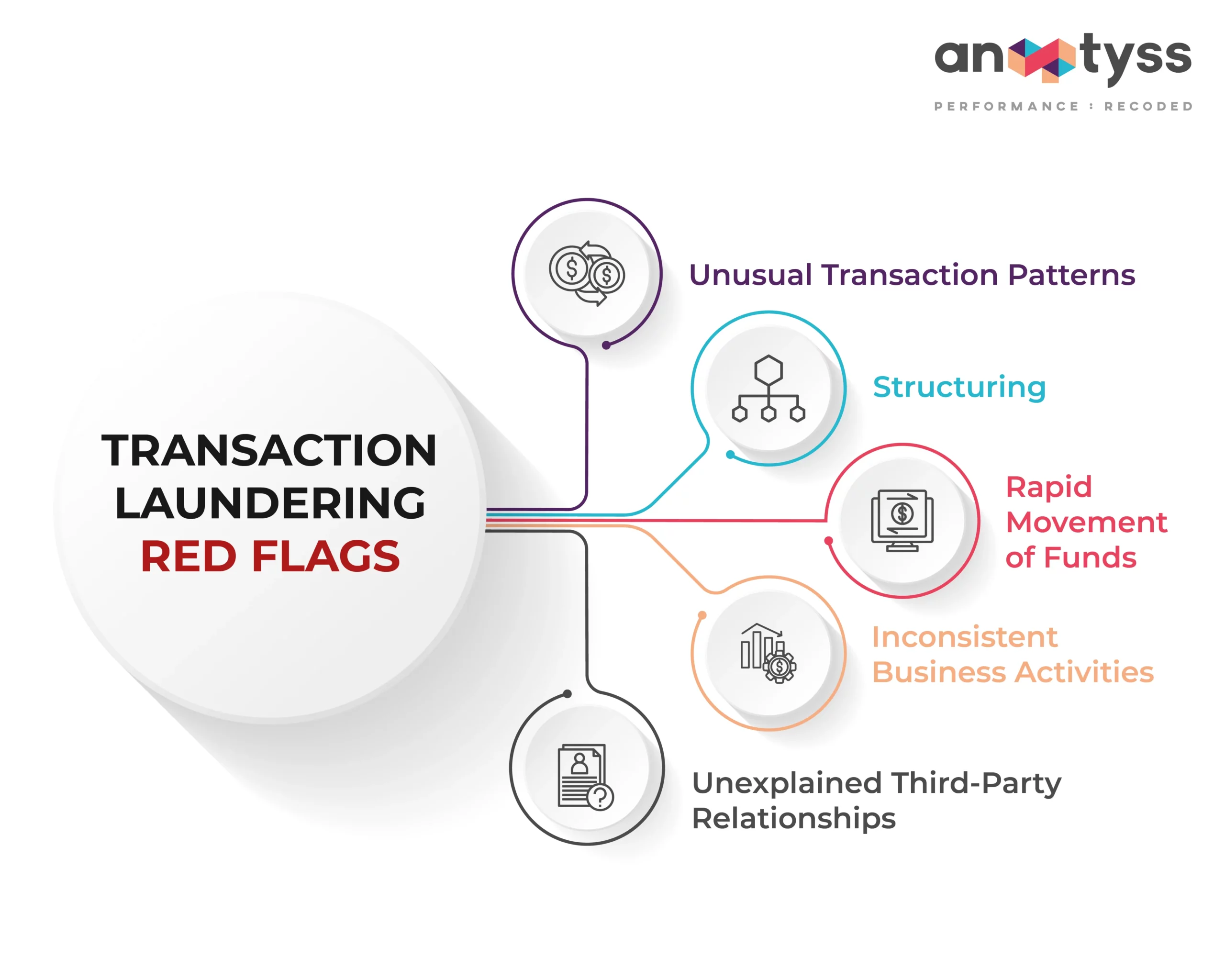
1. Unusual Transaction Patterns
A sudden increase in transaction volumes or a high number of small-value transactions.
2. Structuring
Splitting large transactions into smaller ones to avoid detection.
3. Rapid Movement of Funds
Quick transfers between multiple accounts or jurisdictions.
4. Inconsistent Business Activities
A business engaging in transactions unrelated to its stated purpose.
5. Unexplained Third-Party Relationships
Transactions involving unfamiliar or unverified entities.
By closely monitoring these red flags and implementing robust transaction monitoring systems, businesses can enhance their ability to detect and prevent transaction laundering.
Dive deeper into behavioral red flags with our blog on FATF Red Flags for Money Laundering and Terrorist Financing, a vital reference for frontline AML teams
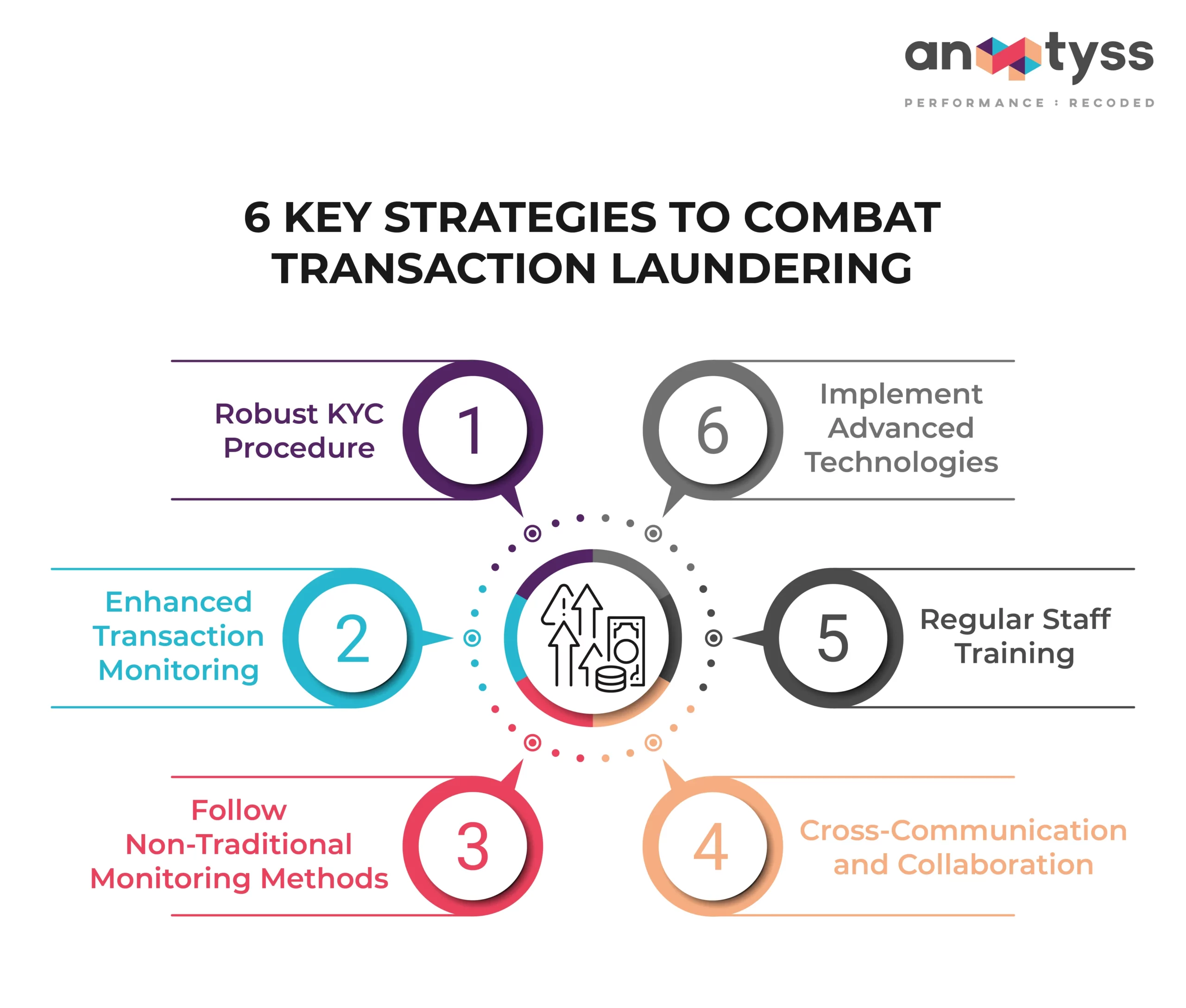
6 Key Strategies to Combat Transaction Laundering
Below are some strategies that financial institutions, including PSPs and MSPs, can employ to fight against transaction laundering.
1. Robust KYC Procedure
Implement thorough KYC processes, including customer due diligence (CDD) and enhanced due diligence (EDD) to verify customer identities, and assess risks and legitimacy of their business activities.
2. Enhanced Transaction Monitoring
Understand the customer risk factors, create rules for each risk, and set up alerts. Also, apply a risk-based approach (RBA), and establish internal controls and policies to determine elements of suspicious behavior and patterns.
3. Follow Non-Traditional Monitoring Methods
Traditionally, banks segregate their customers into high-risk and low-risk categories. Based on their category, the monitoring level is determined. However, low-risk businesses are often targeted for the criminals involved in transaction laundering activities. Therefore, banks need to follow non-traditional monitoring methods to detect and investigate transaction laundering.
4. Cross-Communication and Collaboration
Establish secure platforms to share information and collaborate on identifying and reporting suspicious activities with the state and local law enforcement. With regular and timely updates, banks and law enforcement agencies can keep each other up to date and identify threats proactively.
5. Regular Staff Training
Detecting transaction laundering requires a keen eye for anomalies and suspicious patterns. AML officials and employees need to learn what to look for (red flags) to identify and detect transaction laundering. By training the bank workforce, especially front staff (client servicing), to look for suspicious actions, financial institutions can strengthen their first line of observation while onboarding a customer or entity.
6. Implement Advanced Technologies
Implement and deploy innovative technologies such as advanced analytics with artificial intelligence and machine learning to analyze data sets and identify patterns linked with transaction laundering and money laundering activities. This can help financial institutions enhance the effectiveness of their AML compliance efforts.
Prevent Transaction Laundering and Meet AML Compliance
Transaction laundering poses a significant threat to the integrity of the global financial system. Financial institutions must understand the intricacies of transaction laundering and implement robust AML compliance measures to protect themselves from legal and reputational risks.
See how a US-based bank achieved 75% reduction in false alerts using our proprietary AML solution—proving that intelligent automation works.
An enterprise-grade solution, such as ALFA offers a viable solution for effectively mitigating financial crime risks, including transaction laundering, and complying with AML regulations. It combines the critical aspects in a customized manner to help financial institutions fulfill their AML obligations.
o learn how ALFA can help your financial institution address financial crime risks and AML compliance challenges, reach out to us at: info@anaptyss.com